Integrated solutions for your cybersecurity.
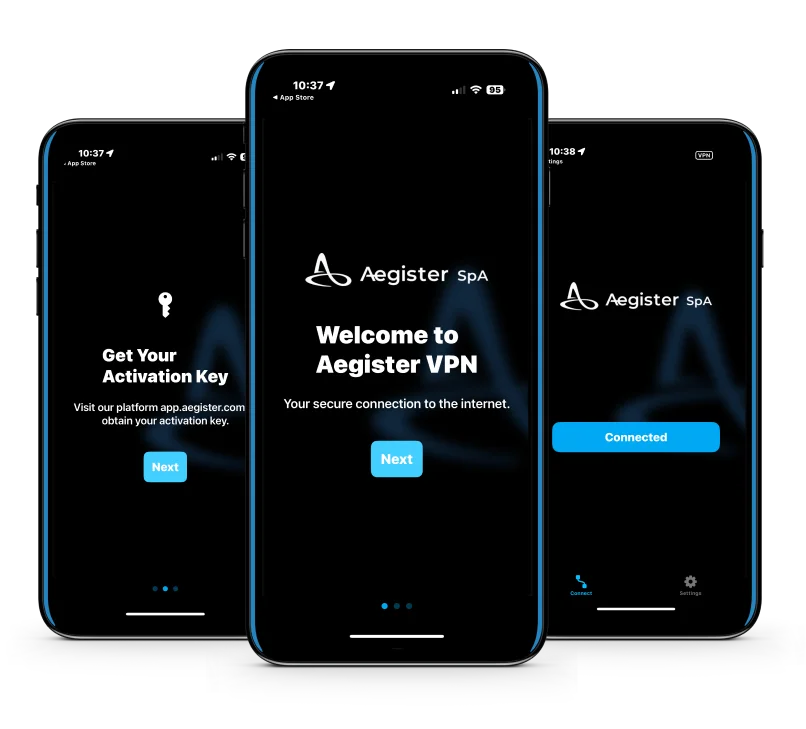
At the core of our services is the Aegister Cyber Console, an integrated platform that serves as a hub for all solutions. With the Virtual CISO as its centerpiece, it includes essential modules such as Risk Assessment, Remediation Plan, and Compliance support. Complementing these are additional Perimeter Protection services like the Aegister Threat Blocker, Cloud Defender, and VPN for comprehensive defense.
Virtual CISO

The Virtual CISO (vCISO) provides companies with a cybersecurity expert who develops security strategies and programs to protect corporate assets, mitigating cyber risks. Ideal for those who cannot hire a full-time CISO, the vCISO offers oversight and guidance for comprehensive security.
LEARN MOREAegister Threat Blocker


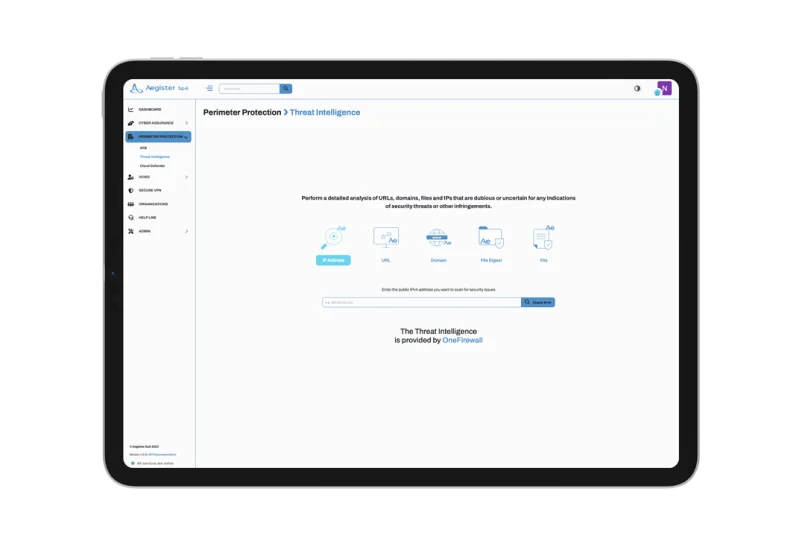
ATB is an Adaptive Firewall with Integrated Intelligence, designed to operate autonomously or complement other systems. Powered by our advanced threat intelligence, ATB detects and blocks threats, providing continuous and optimized protection against cyberattacks.
LEARN MOREAegister Cyber Console
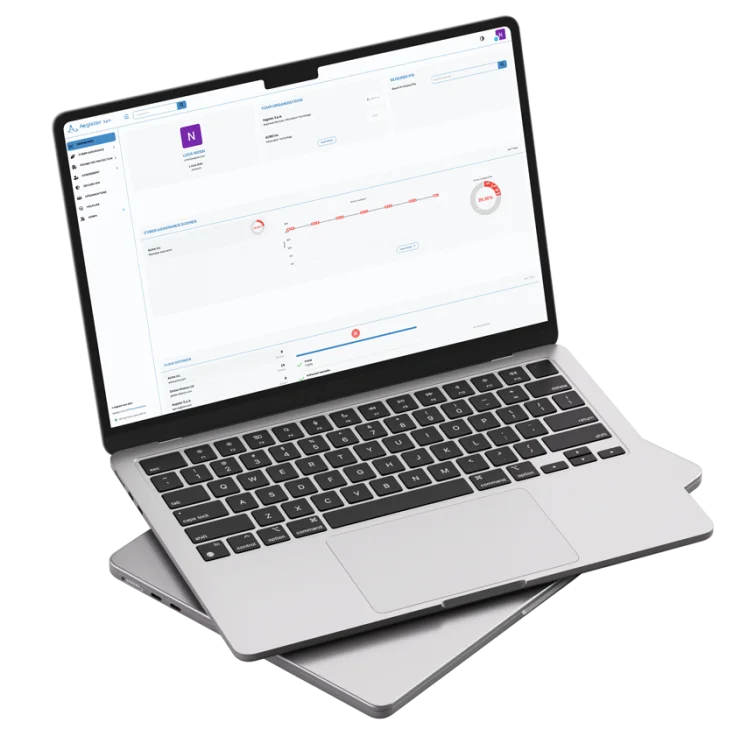
The Aegister Cyber Console (ACC) is the nerve center for all cybersecurity operations, an interactive platform where companies can perform self-assessments, manage tools, and monitor security measures in real time.
Through the ACC, users access the entire suite of Aegister services, with the Virtual CISO as a central element, to assist in risk assessment, compliance, and implementation planning.
Designed to be intuitive, the ACC allows teams to directly interact with their security landscape, monitor metrics, and receive practical guidance from CISOs, making security management simple and comprehensive.

Cloud Defender
Protect your websites and applications with Cloud Defender, a comprehensive and easy-to-manage solution for real-time defense against emerging threats. With advanced rules and our threat intelligence, Cloud Defender automatically detects and blocks attacks like DDoS, SQL injection, and XSS.
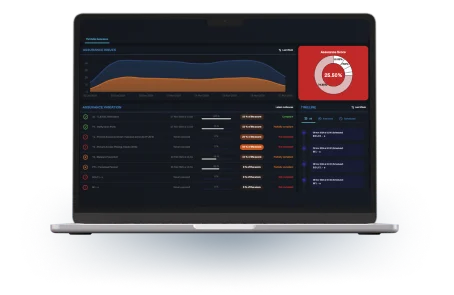
With an interactive dashboard and detailed reports, monitoring security is simple: view attack attempts, respond quickly, and keep your infrastructure secure and compliant. Rely on Cloud Defender for constant, effective, and customizable protection.

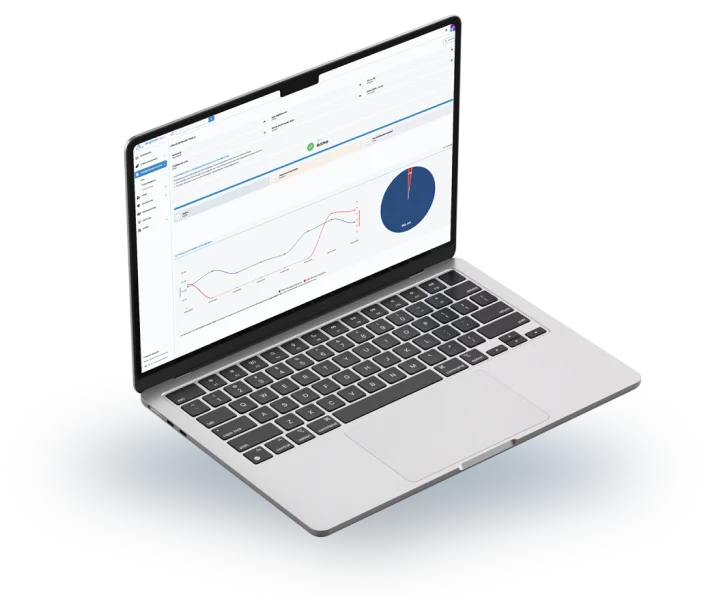
How the WAF Works

Your Comprehensive Compliance Support.
Aegister provides comprehensive compliance support to help companies align with industry standards and regulatory requirements, including the recent NIS 2 directive. Our approach combines expert consulting and automated tools, enabling companies to efficiently manage complex compliance frameworks and maintain continuous compliance with evolving regulations.

Your tailored solution is here.
Aegister's Assessment service offers companies a comprehensive evaluation of their cybersecurity status, identifying vulnerabilities and areas for improvement. Designed to help companies effectively manage risks, the assessment combines advanced tools with expert analysis to deliver a clear and actionable security roadmap.
How it Works
The assessment process starts with a guided survey to collect essential information about the current infrastructure and security practices. Next, our tools perform detailed scans of external assets, analyzing potential exposure points and vulnerabilities. Log analysis is also conducted to identify any past or ongoing anomalies. Finally, Aegister provides a comprehensive report highlighting risks and offering tailored recommendations, giving the company a solid foundation to enhance its security.
GET STARTED