cybersecurity
|compliance
|NIS2
|ACN
|NIS
|registration
|registrazione
|deadline
|scadenza
|28 febbraio
NIS 2026 Reminder: 8 Days Left Before the 28 February Registration Deadline
February 20, 2026
Organizations in scope of Italy's NIS regime have until 28 February 2026 to complete annual registration via the ACN Services Portal. Both new and pr…

cybersecurity
|compliance
|ACN
|Law 90/2024
|Legge 90/2024
|incident taxonomy
|tassonomia incidenti
|NIS
|notification
|Allegato A
ACN Adopts Incident Taxonomy Under Law 90/2024: What Obligated Entities Must Do Now
February 20, 2026
ACN adopted the incident taxonomy under Law 90/2024 via the Determina of 9 February 2026. Obligated entities must now report incidents within 24 hour…

compliance
|NIS2
|EU
|Cybersecurity Act
|ENISA
|supply chain
|certification
|ECCF
|Digital Omnibus
|ICT security
|cybersecurity regulation
|COM(2026) 11
EU Cybersecurity Act Revision – COM(2026) 11: What Changes and Why It Matters
February 05, 2026
The European Commission's January 2026 proposal to revise the EU Cybersecurity Act: supply-chain risk governance, simplified certification (ECCF), EN…

cybersecurity
|VPN
|NIS2
|ransomware
|incident response
|Italy
|DORA
|EU
|GRC
|third-party risk
|digital resilience
|Cybersecurity Act
|ENISA
|supply chain
|edge security
|healthcare
|certification
Cybersecurity Monthly Report – January 2026 (Italy, EU, Global)
January 31, 2026
Aegister’s January 2026 monthly cybersecurity report: EU cybersecurity package with Cybersecurity Act revision and NIS2 simplification amendments, DO…

cybersecurity
|compliance
|CSIRT
|DORA
|finance
|regulation
|resilience
|incident reporting
|Banca d'Italia
|Consob
|IVASS
|COVIP
|third-party risk
|penetration testing
|Virtual CISO
DORA Implementation in Italy: A New Era for Financial Cyber Resilience
June 03, 2025
Italy transposes the EU's Digital Operational Resilience Act (DORA) with new obligations for financial institutions on ICT risk, incident response, a…

incident response
|CSIRT
|EU
|Cyber Solidarity Act
|GRC
|SOC
|cybersecurity policy
|European Commission
|threat detection
|collective defense
The EU Cyber Solidarity Act: A New Pillar of Collective Resilience
May 29, 2025
The EU Cyber Solidarity Act introduces coordinated mechanisms and shared capabilities to improve threat detection, incident response, and strategic r…

cybersecurity
|AI
|threat intelligence
|compliance
|NIS2
|ACN
|cloud security
|ransomware
|incident response
|cyber risk
|Italy
|DORA
|APT
|governance
|IoT
Cybersecurity Update – Week 22 of 2025
May 29, 2025
Aegister's weekly cybersecurity update for Week 22 of 2025, covering major threats, trends, regulatory changes (NIS2, DORA), GRC topics, and internat…

cybersecurity
|NIS 2
|compliance
|ACN
|NIS2 deadline
|italy
|monitoring
|critical infrastructure
NIS 2: Deadline Extension for Companies Until July 31
May 27, 2025
ACN extends the NIS 2 compliance deadline to July 31, 2025, for organizations that have requested support, providing additional time for data updates…

NIS 2
|virtual CISO
|ACN
|cybersecurity compliance
|Regolamento 2690/2024
|cybersecurity baseline
|framework nazionale cyber
NIS 2: Basic Security Measures Defined by ACN for Essential and Important Entities
May 26, 2025
The Italian Cybersecurity Agency (ACN) has published baseline security measures for entities under NIS 2, with operational deadlines and flexibility …

ACN
|ransomware
|cyber threats
|CSIRT
|Italy cyber report
|DDoS
|vulnerabilities
|spear phishing
Cyber Threats in Italy – ACN Operational Summary, April 2025
May 22, 2025
The ACN's April 2025 Operational Summary highlights a rise in ransomware and DDoS attacks in Italy, with key sectors like telecoms and public adminis…
cybersecurity
|compliance
|NIS2
|Direttiva NIS2
|ACN
|obblighi normativi
|scadenza 31 maggio 2025
|Aegister
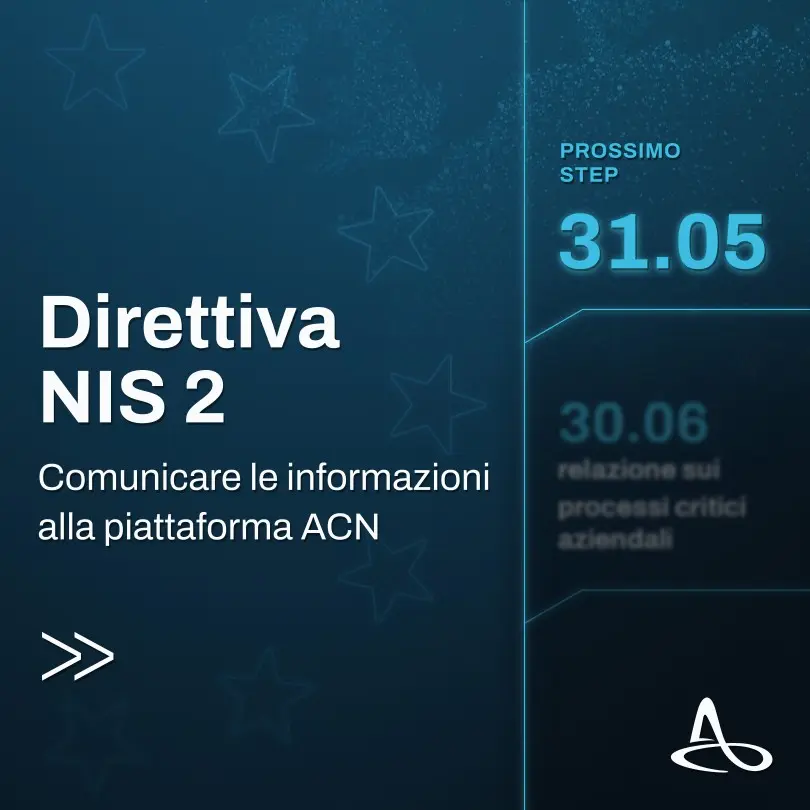
NIS2: Upcoming Obligations for Italian Organizations – Deadline May 31, 2025
May 14, 2025
The NIS2 Directive imposes new responsibilities on Italian organizations classified as essential or important entities. Discover the obligations to b…

ransomware
|cyberattacks
|Italy cybersecurity
|ransomware-as-a-service
|ACN report
|LockBit 3.0
|incident response
Ransomware 2024: Italy Among the Most Targeted Countries
May 08, 2025
Ransomware attacks in Italy surged in 2024, placing the country among the most affected in the world. Find out which sectors are at risk and how to r…
No results found.

threat intelligence
|cloud security
|cloud misconfigurations
|malware in cloud platforms
|GDPR compliance
|NIS2 compliance
|ISO/IEC 27001
|Aegister Cloud Defender
Cloud Security: How Aegister Protects Your Business from Misconfigurations, Malware, and Compliance Risks
May 10, 2025
Discover how Aegister's Cloud Defender enhances your cloud security, addressing misconfigurations, malware threats, and ensuring compliance with GDPR…

cybersecurity
|threat intelligence
|cyber risk analysis
|structured security
|security assessment
|Aegister method
|IT infrastructure
|cybersecurity monitoring
The Aegister Method: A Structured Approach to Cybersecurity
April 29, 2025
Aegister's cybersecurity method is a structured, personalized process designed to protect businesses with precision, starting from risk analysis to c…
No results found.

cybersecurity
|Aegister
|Dubai
|UAE
|GISEC
|GISEC 2025
|digital security
|international partnerships
|MENA
|networking
|fair & exhibition
|events
GISEC 2025: Aegister Closes a New Chapter of Innovation and Global Connections
May 09, 2025
Aegister wraps up its second consecutive participation at GISEC Global 2025, sharing future-driven cybersecurity solutions from stand SP64 in Dubai.

cybersecurity
|Aegister
|Alias S.r.l.
|distribuzione
|partnership
|resilienza digitale
|spin-off universitario
|soluzioni di sicurezza
Aegister Expands Distribution Network Through Strategic Partnership with Alias S.r.l.
May 06, 2025
Aegister S.p.A. announces a new distribution agreement with Alias S.r.l., enhancing its reach in the cybersecurity market through a strategic partner…

cybersecurity
|Aegister
|Dubai
|UAE
|GISEC
|GISEC 2025
|digital security
|international partnerships
|MENA
|networking
|fair & exhibition
|events
Aegister at GISEC Global 2025: Showcasing Cybersecurity Innovation in Dubai
May 06, 2025
Aegister returns to GISEC Global 2025 in Dubai, presenting its latest cybersecurity solutions at stand SP64.

virtual CISO
|cybersecurity leadership
|cyber risk management
|Aegister
|vCISO
|cybersecurity strategy
|CISO-as-a-Service
|compliance support
vCISO by Aegister: Strategic Cybersecurity Without the Full-Time Cost
March 20, 2025
Aegister's vCISO offers strategic cybersecurity leadership tailored to your business without the full-time cost of a traditional CISO.
No results found.

cybersecurity
|virtual CISO
|campania startup 2023
|SMEs
|innovation
|threat blocker
|EU funding
|Aegister project funded under Campania Region grant
June 10, 2024
Aegister S.p.A. has received funding for a cybersecurity project aimed at high-risk SMEs. The project is currently in progress and focuses on develop…
No results found.


EU funding
|ACN
|cybersecurity compliance
|CRA
|PMI
|cascade funding
|SECURE
|Cyber Resilience Act
|open call
|mSME
SECURE First Open Call 2026: What mSMEs Need to Submit Before 29 March 2026
February 20, 2026
The SECURE First Open Call (28 Jan – 29 Mar 2026) offers up to EUR 30,000 per project at 50% co-financing to help mSMEs achieve Cyber Resilience Act …

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|notification
|accountability
|baseline
|roles
|point of contact
|referente
|incident
NIS2 Point of Contact and CSIRT Contact Role: Accountability and Operating Duties
February 18, 2026
NIS2 implementation guidance distinguishes the legal Point of Contact from the operational CSIRT contact role. Practical guide to role formalization,…

cybersecurity
|compliance
|NIS2
|ACN
|supply chain
|baseline
|risk assessment
|GV.SC
|suppliers
|procurement
|contracts
NIS2 Supply-Chain Security: Managing Critical Suppliers and High-Impact Procurements
February 17, 2026
NIS2 supply-chain security is a governance obligation covering supplier identification, risk assessment, contractual integration, and lifecycle monit…

cybersecurity
|compliance
|NIS2
|ACN
|governance
|GRC
|baseline
|evidence
|audit
|documentation
|inventories
|registers
NIS2 Documentary Evidence and Audit Readiness: How to Structure Compliance Proof
February 14, 2026
ACN baseline guidance requires documentary evidence as a core compliance element. Practical guide to evidence families, obligation-to-evidence mappin…

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|notification
|baseline
|significant incident
|IS-3
|service level
|availability
|disruption
NIS2 Significant Incident IS-3: Violation of Expected Service Levels
February 13, 2026
IS-3 in the ACN baseline model covers service-level violation incidents affecting entity services and activities. Practical guide to qualification, s…

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|notification
|baseline
|significant incident
|IS-2
|integrity
|data modification
NIS2 Significant Incident IS-2: Integrity Loss Affecting Digital Data
February 12, 2026
IS-2 in the ACN baseline model covers integrity loss affecting digital data under entity ownership or control. Practical guide to qualification, evid…

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|notification
|baseline
|IS-1
|significant incident
|confidentiality
|data leak
NIS2 Significant Incident IS-1: Confidentiality Loss Affecting Digital Data
February 11, 2026
IS-1 in the ACN baseline model covers confidentiality loss affecting digital data under entity ownership or control. Practical guide to qualification…

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|notification
|baseline
|incident typology
|condition
|compromise
|classification
NIS2 Incident Typology Model: Condition, Compromise, and Affected Object
February 10, 2026
ACN baseline guidance classifies significant incidents through condition, compromise, and object of compromise. Practical guide to using the typology…

cybersecurity
|compliance
|NIS2
|ACN
|resilience
|baseline
|backup
|recovery
|RC
|restore
|continuity
|disaster recovery
NIS2 Recovery Controls (RC): Operational Resilience and Service Restoration
February 07, 2026
The NIS2 Recovery (RC) domain defines how entities restore operations after incidents and sustain resilience. Practical guide to restoration procedur…

cybersecurity
|compliance
|NIS2
|ACN
|CSIRT
|baseline
|response
|RS
|containment
|eradication
|incident handling
|remediation
NIS2 Response Controls (RS): Containment and Eradication in Incident Handling
February 06, 2026
Containment and eradication are iterative response steps that limit damage and remove attacker persistence. Practical guide to strategy selection, ev…

cybersecurity
|compliance
|NIS2
|ACN
|incident response
|CSIRT
|baseline
|escalation
|response
|RS
|signaling
|investigation
|forensics
NIS2 Response Controls (RS): Signaling and Investigation Operating Model
February 05, 2026
The NIS2 Response (RS) domain requires structured incident response through signaling, investigation, and iterative decision loops. Practical guide t…
No results found.