Integrated solutions for your cybersecurity.
The cornerstone of Aegister's offering is the Cyber Console. Designed to serve as a strategic hub, the platform integrates the role of the Virtual CISO, providing comprehensive oversight through dedicated modules, such as Risk Assessment, Remediation Plan, and Compliance support. Complementing the suite, Aegister offers advanced tools for perimeter protection, including the Threat Blocker (ATB), Cloud Defender, and VPN.
Aegister Cyber Console
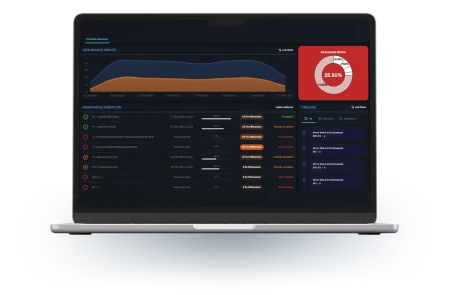
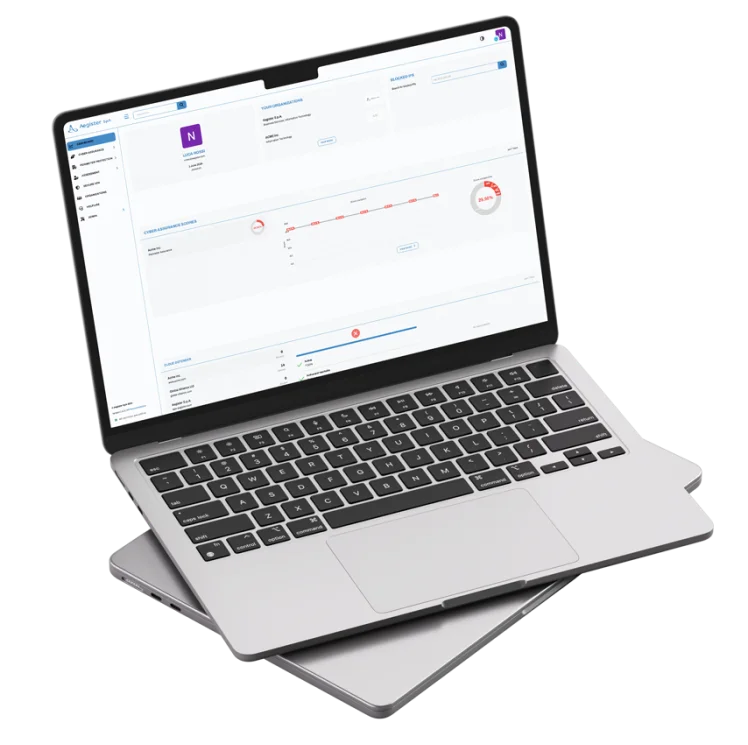
The Aegister Cyber Console (ACC) is the centerpiece of cybersecurity operations, an interactive platform that allows businesses to monitor, manage, and optimize their security strategies in real time.
Integrated with the whole Aegister solution, the ACC provides advanced functionalities for risk assessment, regulatory compliance management and planning of targeted corrective actions.
Thanks to an intuitive interface, the ACC allows in-depth analysis of the corporate security ecosystem, monitoring of critical metrics, and strategic support from the Virtual CISO, ensuring effective cybersecurity management aligned with the highest standards.


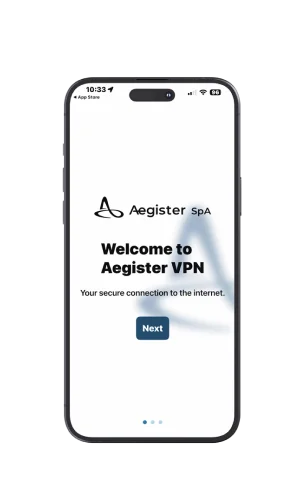
Aegister VPN
AegisterVPN is an advanced data protection solution that operates on Android and iOS to ensure secure and encrypted connections. It creates a private tunnel to the Aegister VPN server, supported by Threat Intelligence, that keeps your connection secure and private regardless of whether you are on a corporate or remote network.
Cloud Defender
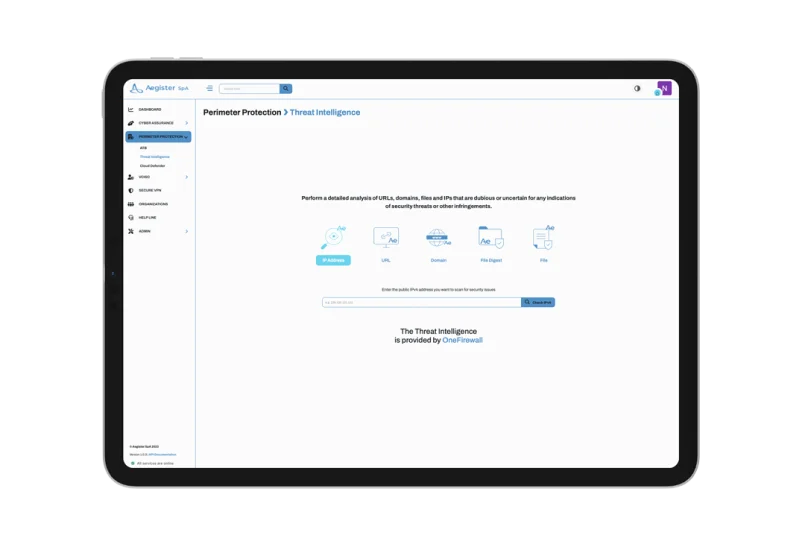
Aegister Cloud Defender is an advanced Web Application Firewall (WAF) designed to protect web applications from common threats and mitigate the OWASP Top 10 risks, such as SQL injection, cross-site scripting (XSS), and DDoS attacks.
With customizable rules continuously updated via Threat Intelligence, the system analyzes HTTP/HTTPS traffic in real time, automatically detecting and blocking anomalous and potentially harmful behaviors.
The dashboard enables monitoring of critical metrics, such as block rates and traffic sources, facilitating timely interventions and optimization of security rules.
This multicloud solution leverages resources from various globally distributed providers to optimize performance, enhance resilience, and ensure low latency, offering an improved user experience while mitigating risks associated with reliance on a single cloud provider.


How the WAF Works

Your Comprehensive Compliance Support
Compliance with cybersecurity regulations is crucial to gain trust, to avoid operational disruptions, reputational damage, legal actions, and avoid fines caused by cyberattacks. The NIS 2 Directive, entered into force in October 2024, include a significantly larger number of companies compared to the previous NIS, including small and medium-sized enterprises in specific sectors, which will need to implement security measures in various areas to strengthen their cyber resilience.

Incident Management

Supply Chain Security

Encryption Usage Policies and Procedures

Use of Multi-Factor Authentication Solutions

Basic Cyber Hygiene Policies and Training

Information and Network Systems Security

Risk and Security Assessment Policies

Strategies for Assessing Risk Management Measures

Business Continuity and Disaster Recovery

HR Security

Your tailored solution is here.
Aegister's Assessment service offers companies a comprehensive evaluation of their cybersecurity status, identifying vulnerabilities and areas for improvement. Designed to help companies effectively manage risks, the assessment combines advanced tools with expert analysis to deliver a clear and actionable security roadmap.
How it Works
The assessment process starts with a guided survey to collect essential information about the current infrastructure and security practices. Next, our tools perform detailed scans of external assets, analyzing potential exposure points and vulnerabilities. Log analysis is also conducted to identify any past or ongoing anomalies. Finally, Aegister provides a comprehensive report highlighting risks and offering tailored recommendations, giving the company a solid foundation to enhance its security.


Assessment