The Aegister Method: A Structured Approach to Cybersecurity
April 29, 2025
Digital security isn't improvised. It's built step by step.
At Aegister, we follow a structured, personalized approach to cybersecurity. Every organization has unique characteristics, technologies, and risk levels. That's why applying a clear methodology makes the difference. With the NIS2 compliance deadline approaching, our method helps organizations meet regulatory requirements while maintaining robust security. Here's how we work:
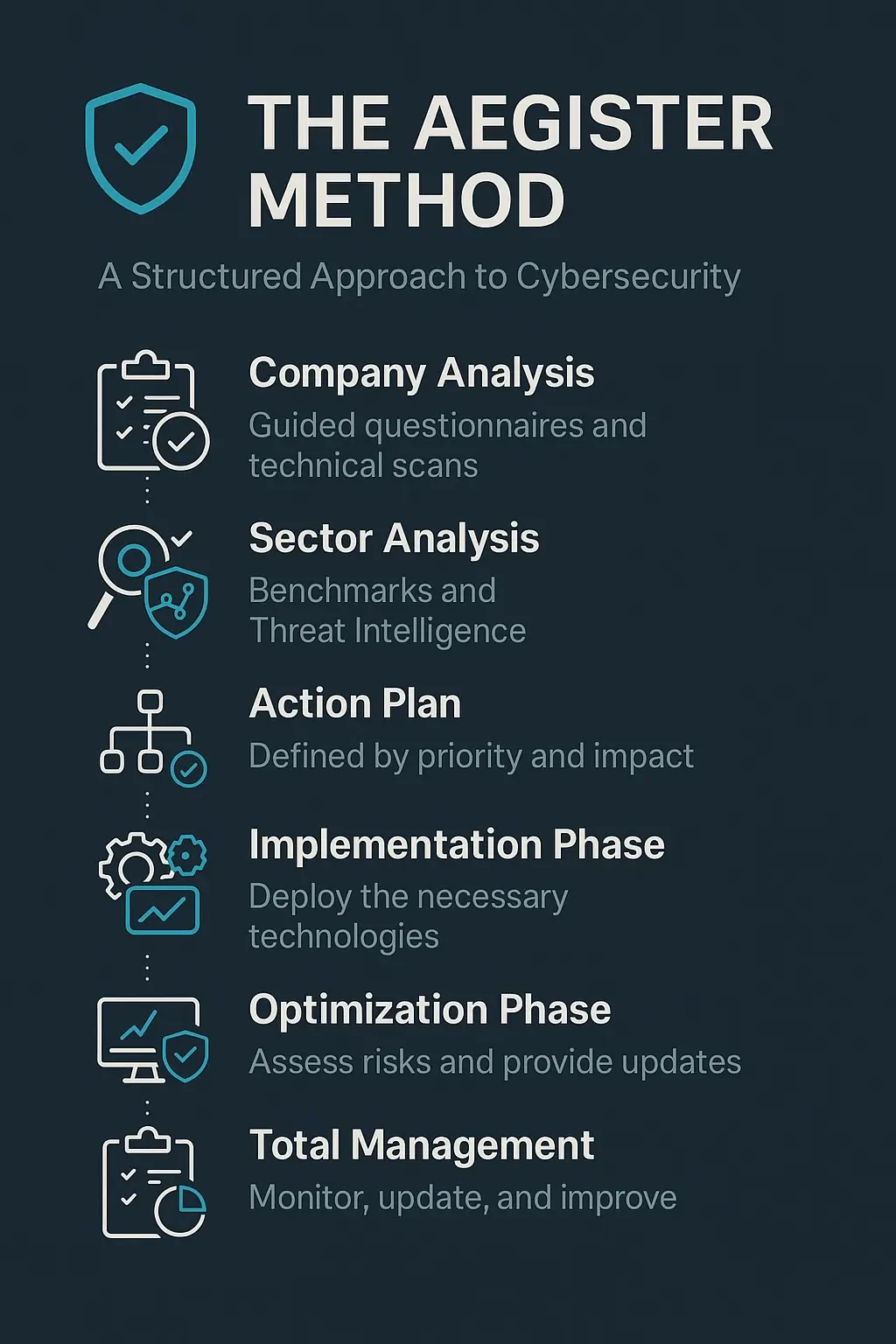
- Company Analysis: We begin with guided questionnaires and technical scans to identify vulnerabilities and understand the critical points of your infrastructure.
- Sector Analysis: We incorporate regulatory frameworks, benchmarks, and Threat Intelligence, creating tailored policies. This includes NIS2 baseline security measures for organizations in scope.
- Action Plan: We define a clear intervention plan organized by priority and impact nothing is left to chance. Our NIS2 compliance guide helps organizations navigate the requirements effectively.
- Implementation Phase: We deploy the necessary technologies, ensuring seamless integration with your existing systems.
- Optimization Phase: We assess risks, assign criticality scores, and ensure real-time updates and alerts.
- Total Management: We continuously monitor, update, and improve the system, delivering timely and complete reports. Organizations can leverage our Virtual CISO service for ongoing compliance and security management.
With Aegister, cybersecurity is not just an option it's a strategic journey built on a proactive and protective foundation tailored to your operations.